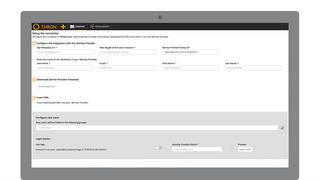
SAML Connector has been developed to allow companies using an Identity Management system to manage Platform authentication via Single-Sign-On based on SAML 2.0 protocol. The connector provides the synchronization capabilities of users and groups from the IdP system to THRON via SCIM protocol. Users provided through this procedure will automatically be enabled to authenticate in Single-Sign-On. Thanks to this integration, both Platform authentication and identity management will be entirely managed outside THRON and within the corporate Identity Provider.
Requirements
The SAML Connector has the following requirements:
- An IdP installed by the customer that supports SAML 2.0 protocol
- The SAML Connector, properly configured in THRON.
- [Optional] For users and group provisioning, support for SCIM 2.0 protocol.
All the information needed to configure the connector and its integration with your Identity Management system are available in this article: https://help.thron.com/hc/en-us/articles/360023785573-How-to-configure-SAML-Connector
Application provided by: THRON S.p.A.
Website: www.thron.com
Contacts:
- Mail: marketplace@thron.com
- Tel.: (+39) 049.5599777
- Fax: (+39) 049.5599779
Current version: 1.0